What we cover
What is Security Information and Event Management (SIEM)?
Security Information and Event Management (SIEM) solutions have become indispensable tools for security teams today. As organizations adopt cloud services, mobile devices, IoT and expand networks, the volume and complexity of security data grows exponentially. Meanwhile, cyber threats are more advanced than ever, with attackers adept at evading traditional defenses. This combination puts immense strain on security staff struggling with too many alerts, too little context, and too little expertise.
Effective SIEM platforms help address these challenges through log management, correlation analysis, anomaly detection, threat intelligence, and workflow automation. By collecting, contextualizing and analyzing security data, SIEMs enhance threat visibility, streamline investigations and empower resource-constrained teams. Worldwide SIEM adoption continues to grow, with the global market projected to reach $7.9 billion by 2027. For most organizations, SIEMs are no longer “nice to have” but a fundamental component of security stacks.

What is Security Information Management (SIM)?
SIEM platforms ingest data from across the IT environment, securely store that data, analyze it for threats, and trigger appropriate responses. Core capabilities include:
- Log Management: Collecting and centralizing logs from network gear, security tools, servers, databases, applications etc. This provides broader visibility.
- Aggregation: Taking log data from disparate sources and formatting it into a common data structure for analysis.
- Normalization: Mapping raw log fields like IP addresses, ports, users etc. to a consistent schema. This enables correlation.
- Correlation analysis: Applying analytics like rules, statistical models and machine learning to connect related events across data sources and identify incidents.
- Alerting: Generating notifications when a correlation rule, threshold or anomaly is triggered to inform security teams.
- Visualization: Presenting analytical findings, incidents and KPIs in dashboards, graphs and reports to provide actionable insight.
- Workflow automation: Using predefined playbooks to automatically execute response actions like blocking users or quarantining endpoints when threats are detected.
Under the hood, SIEM architecture consists of collectors, a central data store, analytics engines and user interfaces. Collectors gather data via APIs, agents or polling/sniffing network traffic. That raw data gets aggregated and normalized before entering the data store, which is typically a specialized database optimized for time-series data. Analytics engines then process the structured data to detect outliers, link events, identify threats etc. These findings get visualized via dashboards, alarms, reports and workflow tools.
Typical data sources for SIEM platforms include:
- Firewalls, IDS/IPS, proxies, load balancers, routers
- Endpoint security agents
- Virtualization infrastructure
- Cloud services like IaaS, PaaS, SaaS
- Identity providers
- Database activity
- File integrity monitoring
- Email servers
- Custom applications via APIs
With normalized data from these sources, SIEMs can provide comprehensive visibility and behavioral analysis for security teams.
How does it work?
Let’s look at how SIEM platforms actually process and analyze data:
- Ingestion: SIEMs use agents, connectors and APIs to bring in streams of log data from across an environment. Support for common protocols like Syslog ensures interoperability. Connectors can preprocess data before it enters the system.
- Normalization: Once ingestion pipelines are established, the raw data gets normalized into a consistent format. For example, time stamps get converted to a standard time zone and events from different vendors get mapped to shared fields and descriptions.
- Enrichment: Context like asset criticality, known vulnerabilities and threat intelligence can be added to events to enable risk-based prioritization. Usernames may get resolved to real identities.
- Storage: Normalized events land in the SIEM database, which is optimized for fast queries, ETL processing and scalability. Native compression minimizes storage overhead.
- Baselining: Machine learning models profile normal behavior of users, systems and networks to detect meaningful anomalies.
- Correlation analysis: The SIEM applies rules, statistical models and algorithms to connect lower-level events into incidents and detect patterns indicative of breaches, policy violations etc.
- Alerting: Thresholds and correlation results trigger notifications via email, SMS etc. to instantly inform security teams about high priority threats.
- Reporting: Historic data provides visibility into trends via graphs, charts and tables. Reports help demonstrate compliance controls.
- Response workflows: Predefined playbooks can automatically execute containment actions like locking accounts, isolating systems, blocking IP addresses etc. when certain criteria are met.
These capabilities working together enable comprehensive detection, informed investigations and rapid response. Customizable rules, advanced behavioral analytics and machine learning maximize threat visibility. Automated workflows accelerate incident response. Expert security teams can fine tune the platform to fit their organization’s needs and workflows.
How much do they cost?
SIEM solutions range dramatically in price from under $1,000 to over $1 million depending on included capabilities and deployment scale. Core pricing models include:
- Perpetual license: An upfront license cost for on-premises infrastructure, plus ongoing maintenance fees for support and updates.
- Subscription: Annual fees for cloud-delivered or on-prem SIEM that includes maintenance and support.
- SaaS: Pay-as-you-go pricing for SIEM software provided as a cloud service. Usage-based pricing scales with data volume.
Other pricing factors include:
- Number of log sources
- Data volume per day
- Speed of ingestion
- Data retention duration
- Analytical features like machine learning
- Visualization complexity and customization
- Workflow automation and response playbooks
- Ongoing maintenance, tuning and support
Entry-level SIEM tools aimed at SMBs typically start around $1,000 – $5,000 annually depending on log sources. Mid-range enterprise SIEM platforms can cost $15,000 – $25,000 for a mid-size deployment. High-end solutions for large global organizations run $50,000 – $500,000+ per year.
Additional costs like professional services, scaling fees and maintenance can make the total cost of ownership 2-4X the initial software price. Cloud services allow more pay-as-you go flexibility whereas on-prem needs long term capacity planning.
How to evaluate and choose the best SIEM tools?
Choosing the right SIEM platform is crucial but can be challenging with hundreds of tools on the market. Here are key factors to consider when selecting a SIEM:
- Coverage: Ensure the SIEM integrates with all the required data sources like firewalls, IDS/IPS, endpoints, cloud apps, etc.
- Analytics: Prioritize SIEM tools with strong analytics and intelligence to detect advanced threats. UBA and machine learning capabilities are ideal.
- Ease of use: The interface, alerts, and reporting should be intuitive and easily customized. Complex tools lead to poor adoption.
- Scalability: Choose a platform built to handle your current and future data volumes as your needs grow over time.
- Compliance: If regulatory compliance is a priority, verify the SIEM has templates and reporting for relevant standards like PCI DSS, HIPAA, etc.
- Context: SIEMs that link events with threat intelligence, vulnerabilities, users, assets, etc provide deeper context for effective incident response.
- Develop requirements: Document existing infrastructure, data sources, log volumes, compliance needs and use cases. Engage security, IT and compliance teams to get input. Prioritize must-have capabilities.
- Compile vendor list: Research analyst reports like Gartner MQ and crowdsourced review sites to curate a list of vendors that align with your requirements.
- Evaluate shortlist: Ask vendors to demonstrate core functionality, customization, scalability etc. relevant to your needs. Compare solutions across key criteria.
- Request proposals & pricing – Ask 2-3 leading candidates to respond to an RFP outlining capabilities, services, total costs etc.
- Run POCs: Setup pilots of the top solutions using production data and use cases. Focus on ease of deployment, quality of detection, actionable insights etc.
- Select & negotiate: Choose the optimal platform based on performance, TCO and vendor partnership opportunity. Negotiate final pricing and contract terms.
- Tune & expand: Roll out SIEM to priority areas first, then tune rules and analytics before expanding across the organization.
Avoid common pitfalls like:
- Overbuying far beyond current needs and maturity level
- Getting distracted by bells & whistles vs. core functionality
- Relying on consultants without internal expertise
- Choosing mainly on price, not capabilities or vendor fit
- Poor long term vendor support and partnership
Matching organizational maturity, budget and requirements with vendor strengths and pricing tiers is essential for SIEM success.
Best SIEM Tools
Best SIEM Tools – At a glance
| Criteria | SolarWinds | Graylog | LogRhythm | IBM Security QRadar | Splunk | Fusion SIEM | Sumo Logic | McAfee | Salesforce | Rapid7 InsightIDR |
| Best For | SMBs | Open Source | Large Enterprise | Large Enterprise | Large Enterprise | MSSPs | Cloud-Native | Mid-Market | Compliance | Mid-Market |
| Ease of Use | High | Medium | Medium | Medium | Medium | High | High | Medium | Low | High |
| Pricing | $ | Free | $$$ | $$$ | $$$ | $$ | $$ | $$ | $$$ | $$ |
| Scalability | Medium | High | High | High | High | Medium | High | Medium | High | High |
| Threat Detection | Low | Medium | High | High | High | Medium | Medium | Medium | Medium | High |
| Compliance Reporting | Low | Medium | High | High | High | Medium | Medium | High | High | Medium |
| Cloud Support | Low | Medium | Medium | Medium | High | High | High | Medium | High | High |
| Incident Response | Low | Medium | High | Medium | High | Medium | Medium | Medium | Low | High |
| UBA Capabilities | Low | Medium | High | Medium | High | Medium | Medium | Medium | Low | High |
| Ecosystem Integration | Low | Medium | High | High | High | Medium | Medium | Medium | Medium | Medium |
Best SIEM Tools – Let’s dive deeper
Let’s now dive deeper into each of the SIEM Tools on our list.
1. SolarWinds Security Event Manager
SolarWinds Security Event Manager (SEM) is an affordable and easy to use SIEM platform designed for SMBs.
- Key Features: Predefined correlation rules, log management, basic reporting
- Price: Starts at $1,995 per year for up to 100 nodes
- Reviews & Ratings: 4/5 stars on Gartner Peer Insights based on 39 reviews
- Pros: Simple interface, fast deployment, automated threat response
- Cons: Limited analytics, minimal compliance support, not scalable for large orgs
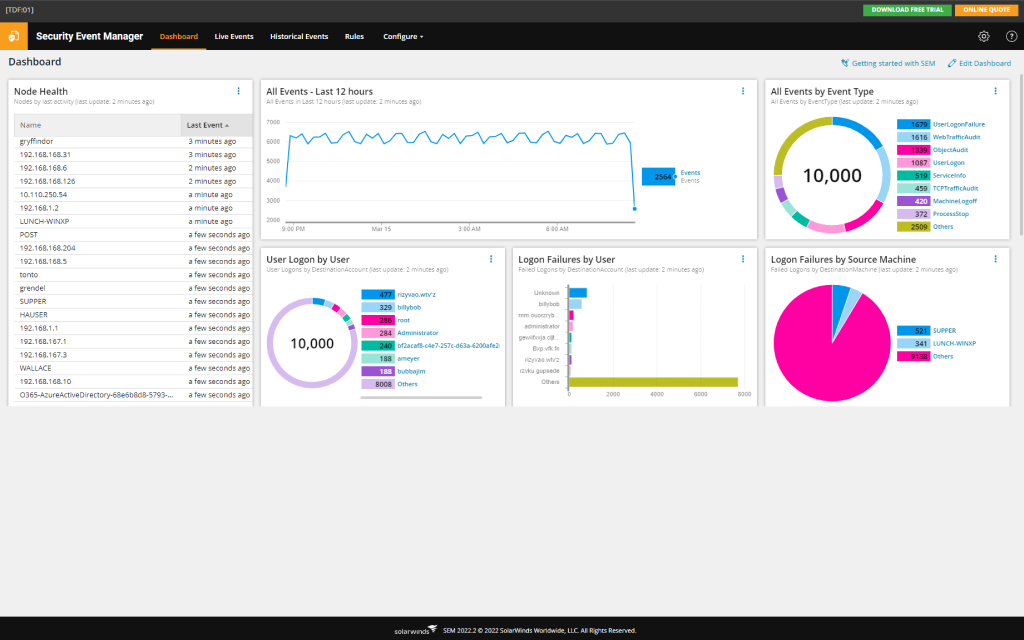
SolarWinds Security Event Manager (SEM) provides an affordable and easy-to-use SIEM platform purpose-built for smaller organizations. SEM offers essential SIEM capabilities including central log management, basic correlation rules, threat monitoring dashboards, and compliance reporting. The software is designed for rapid deployment through an intuitive web interface, preconfigured dashboards, and template compliance reports for standards like PCI DSS. SEM tightly integrates with additional SolarWinds tools for network and systems management, enhancing visibility further across the IT infrastructure.
However, SEM lacks more advanced detection capabilities like user behavior analytics and robust threat intelligence. The platform has minimal options for custom threat modeling, intelligent correlation or machine learning. Compliance support is mostly out-of-the-box rather than customizable, dashboards are not highly flexible, and the overall feature set trails leading enterprise SIEMs. SEM is also limited in scalability, supporting around 100 nodes maximum.
SolarWinds SEM works best for smaller organizations with relatively basic SIEM requirements needed mainly for log consolidation, security monitoring and basic compliance. For larger enterprises or those with sophisticated security use cases, SEM’s technical limitations could constrain long term success and growth. But for SMBs who just need fundamental SIEM capabilities quickly and affordably, SEM represents an accessible starting point.
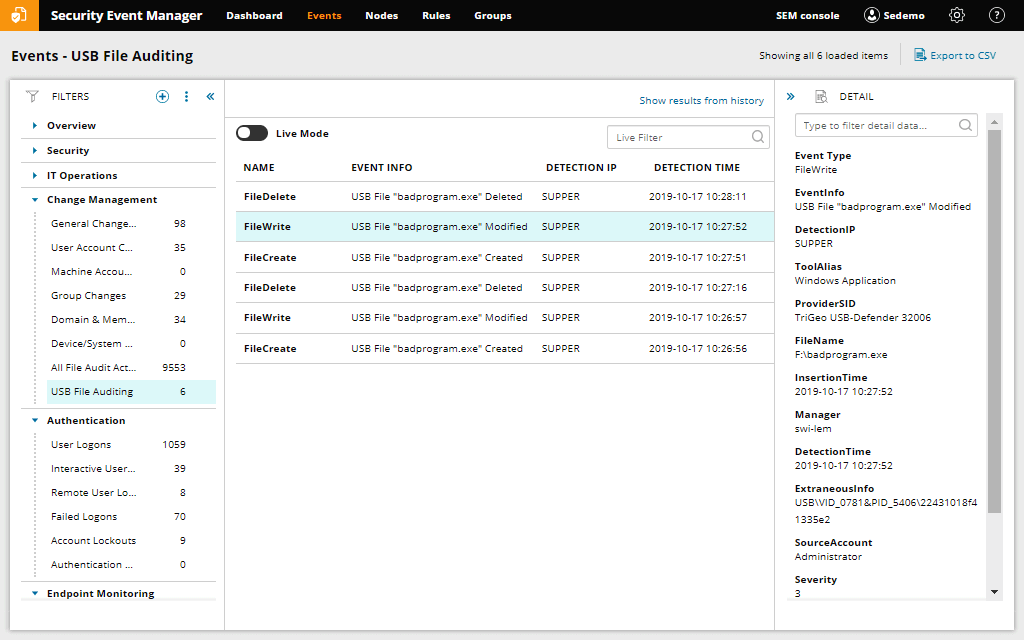
Key Features
- Pre-built correlation rules to detect common threats out of the box
- Automated responses like shutting down access upon threat detection
- Intuitive web interface and templated reports for easy usability
- Continuous log collection and retention policies
Why You Should Consider
SolarWinds SEM is a top choice for SMBs that want affordable, entry-level SIEM with fast implementation.
2. Graylog
Graylog is a popular open source SIEM platform built for scalability and flexibility.
Key Features: Custom correlation rules, enriched threat intelligence, UBA features
- Price: 100% free and open source
- Reviews & Ratings: 4.2/5 stars on Capterra based on 218 reviews
- Pros: Free to use, scalable to large environments, open source flexibility
- Cons: Steep learning curve, lacks out of the box compliance features
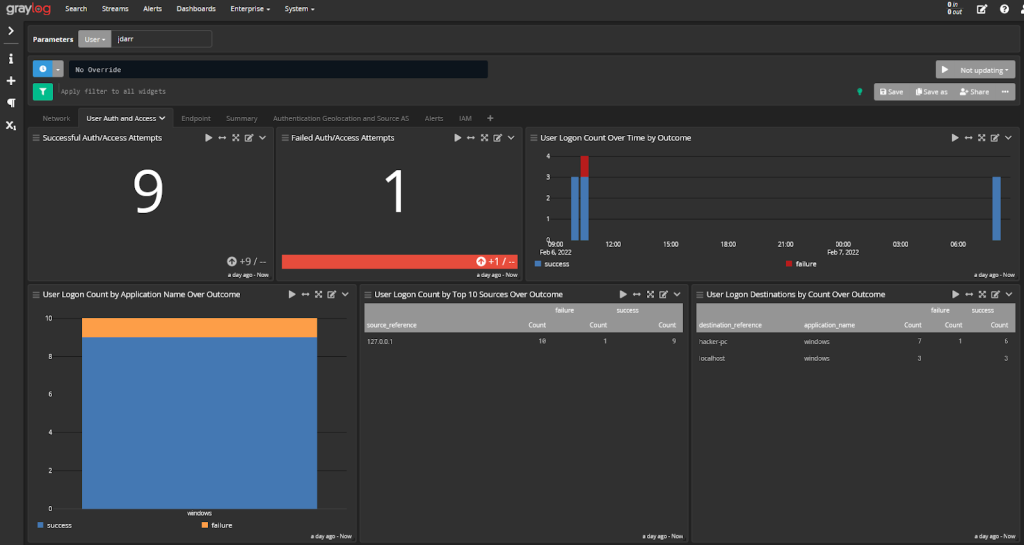
Graylog, an open-source SIEM platform, stands out for its scalability, flexibility, and value, especially for expert security teams. Specializing in high-throughput log management, it can handle terabytes of data daily, making it suitable for large, complex environments. Its optimized search and analytics architecture enables rapid queries across extensive historical data, and users often commend its data exploration and threat hunting capabilities.
Despite its strengths, Graylog’s open-source nature means it lacks some features found in commercial competitors. The interface and workflows can be challenging to master, and compliance reports are limited. Significant in-house expertise is required for setup and utilization, with community support replacing dedicated vendor resources.
Graylog is best suited for large enterprises with skilled security analysts. While it offers flexibility and scale at zero license cost, its full potential is realized by expert teams capable of customization.
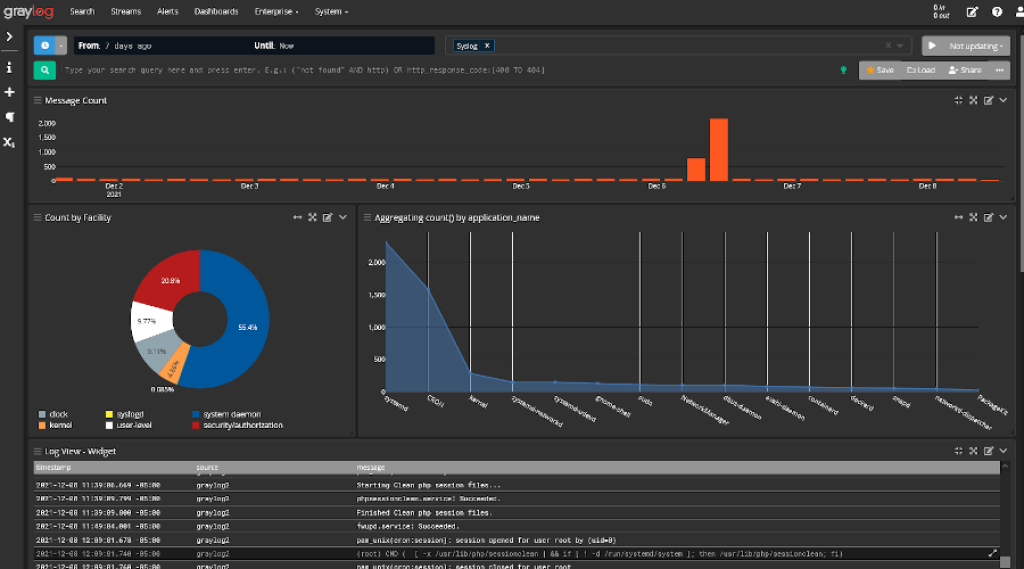
Key Features
- Scales to process terabytes of data per day
- Flexible open source architecture with over 500 plugin integrations
- Correlation engine to identify threats from low level alerts
- Machine learning and behavioral analytics capabilities
Why You Should Consider
Graylog excels at scalability and flexibility, making it a top open source choice suitable for large, complex environments.
3. LogRhythm
LogRhythm is an enterprise-ready SIEM providing comprehensive analytics, intelligence, and compliance.
- Key Features: UBA, network monitoring, integrated threat intelligence
- Price: Starts around $25,000 annually for entry level
- Reviews & Ratings: 4.4/5 stars on Gartner Peer Insights based on 70 reviews
- Pros: Advanced threat detection, ease of use, compliance coverage
- Cons: Very expensive, resource heavy, steep learning curve
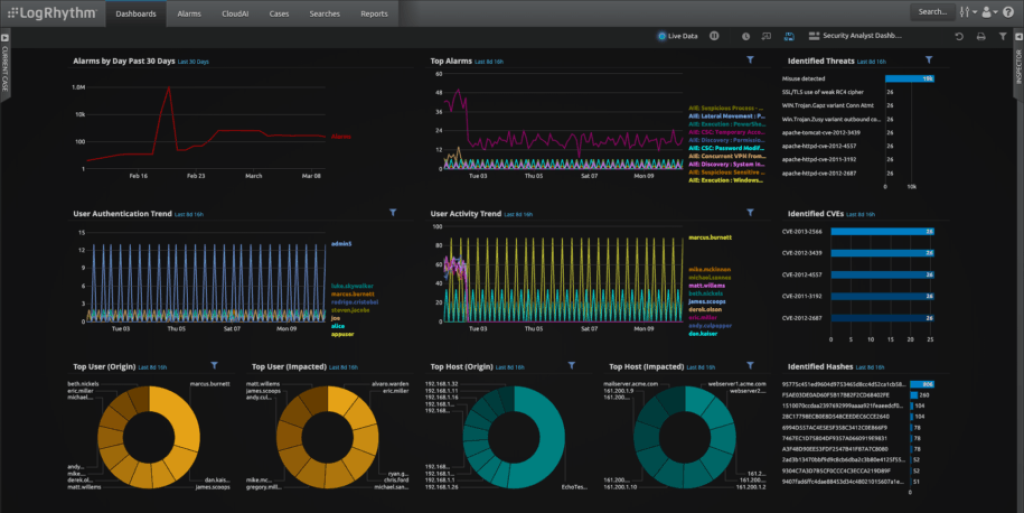
LogRhythm, a premium SIEM platform, is known for detecting sophisticated threats like compromised accounts and insider risks. Its core AI Engine profiles user behavior, offering advanced analytics to uncover abnormal activities. LogRhythm also provides extensive compliance reports for standards like PCI-DSS and HIPAA.
The platform’s advanced capabilities come with a hefty price tag, starting around $25,000 annually for medium-sized organizations. It’s also resource-intensive and can be challenging for junior analysts to learn.
LogRhythm excels in advanced threat detection and compliance expertise but requires significant investment in licensing and infrastructure. It’s best suited for large security teams that can utilize its sophisticated features, which may exceed the needs of smaller organizations.
Key Features
- Behavioral analytics to detect insider threats and compromised accounts
- Compliance reporting templates for standards like PCI DSS, HIPAA, GLBA
- Network detection engine for deep traffic inspection
- Integrated threat intelligence feeds
Why You Should Consider
LogRhythm leads in advanced threat detection, intelligence, and ease of use, making it the go-to enterprise SIEM.
4. IBM Security QRadar
IBM QRadar provides an integrated SIEM and security analytics platform.
- Key Features: Anomaly detection, incident forensics, dedicated appliance option
- Price: Starts around $30,000 annually
- Reviews & Ratings: 4.2/5 stars on Gartner Peer Insights based on 89 reviews
- Pros: Scalable to enormous data volumes, powerful hunting capabilities
- Cons: Complex interfaces, expensive licensing model
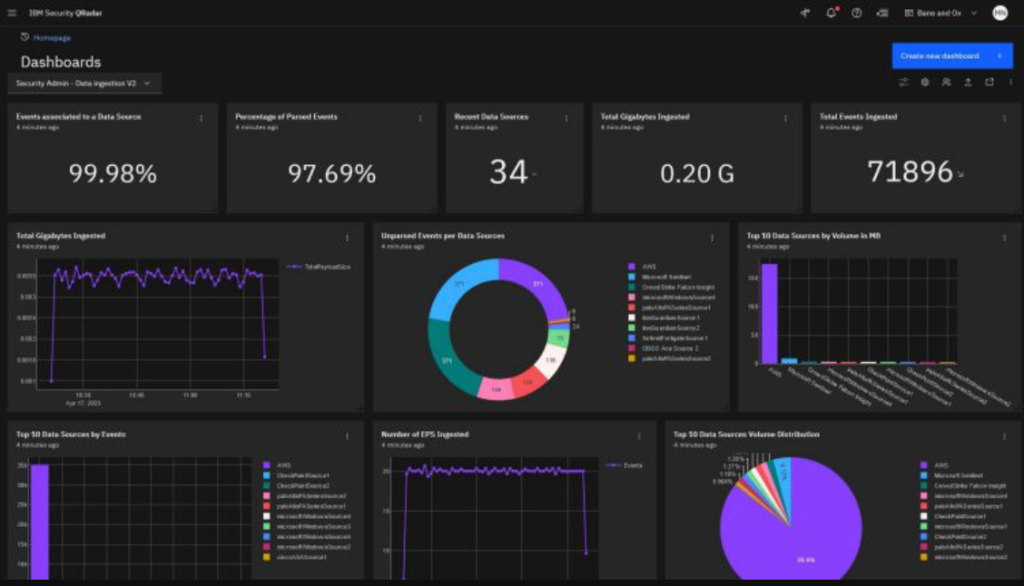
IBM QRadar provides a highly scalable SIEM platform capable of handling hundreds of thousands of events per second, positioning it for enormous global enterprises. As part of the wider IBM Security intelligence platform, QRadar integrates tightly with both on-prem and cloud-based IBM security products, augmented by Watson AI and threat intelligence. Customers praise QRadar’s broad log management capabilities and rapid threat identification.
Still, QRadar presents a steep learning curve even for experienced analysts, given the immense configuration options and workflow customization possible. The tool demands significant expertise to master. Licensing follows a consumption-based model which can become expensive for larger customers with massive data flows. QRadar works best for organizations invested into the broader IBM security ecosystem who can take advantage of its integration and joint capabilities.
QRadar offers market-leading scalability, security analytics via Watson AI, and integrated threat intelligence feeds making it a potential SIEM choice for large enterprises. But functionality comes at the cost of high complexity. For smaller firms or those new to SIEM, QRadar’s sophistication likely exceeds current needs.
Key Features
- Dedicated QRadar appliances for on-prem deployment
- Anomaly detection using intelligent baselining of activity
- Security analytics powered by Watson AI and machine learning
- Graphical forensics for threat hunting and investigations
Why You Should Consider
IBM QRadar offers market-leading scalability and forensics powered by Watson AI, appealing to data-driven enterprises.
5. Splunk
Splunk provides a premium SIEM platform focused on big data and analytics.
- Key Features: Big data analytics, custom dashboards, AI-driven investigation
- Price: Starts around $20,000 annually
- Reviews & Ratings: 4.4/5 stars on Gartner Peer Insights based on 246 reviews
- Pros: Powerful analytics, flexible customization, industry-leading scalability
- Cons: Very expensive, complex navigation, resource intensive
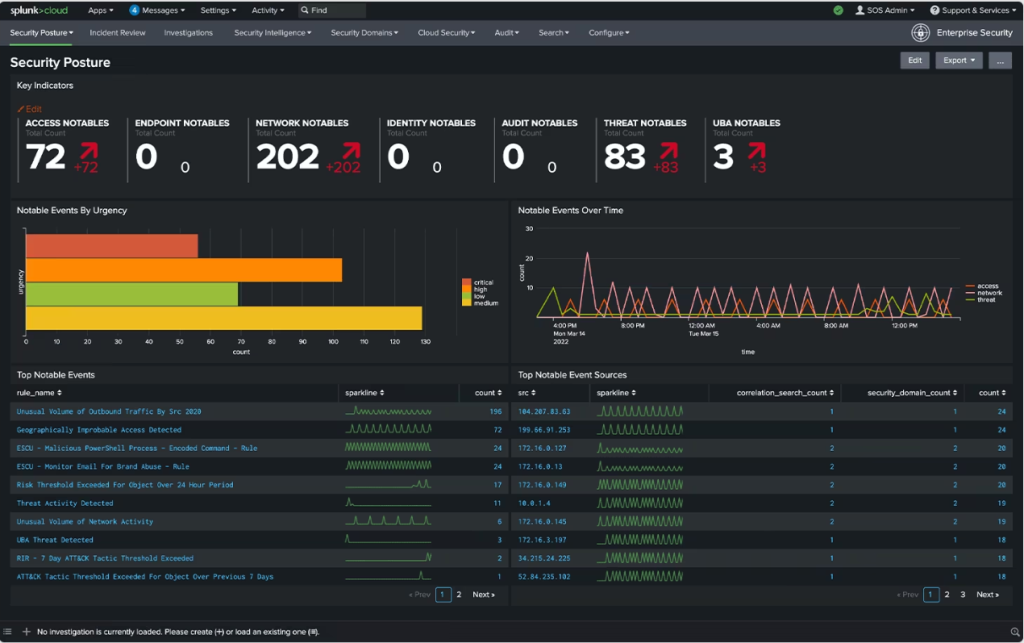
Splunk Enterprise leads the high-end SIEM market with its scalability (up to petabytes of daily ingestion) and advanced analytics powered by machine learning. It’s praised for its flexible data intake, broad security tool integrations, customizable dashboards, and robust correlation capabilities.
Splunk’s complexity requires expertise in both development and interpretation, and tuning it for optimal incident detection can be challenging. Its extensive capabilities may exceed the needs of organizations with more basic requirements.
Splunk Enterprise delivers premium SIEM focused on big data analytics and scaling to security teams who can leverage its sophistication. But smaller firms may find deploying and managing Splunk overwhelming and fail to realize value commensurate with its high costs. For advanced security analytics at massive scale, Splunk leads the market.
Key Features
- Petabyte-scale data ingestion and analytics
- Customizable dashboards tailored to unique workflows
- AI-driven investigations and user behavior analytics
- Over 2,200 third-party integrations and apps
Why You Should Consider
Splunk leads the market in big data security analytics, though the extensive capabilities come at an enterprise price tag.
6. Fusion SIEM
Fusion SIEM is a cloud-based SIEM platform built for MSSPs and MSPs.
Key Features: Multi-tenant architecture, unified dashboards, automated threat response
- Price: Starts at $7 per month per device
- Reviews & Ratings: 4.7/5 stars on Capterra based on 15 reviews
- Pros: Cloud delivery model, affordable pricing, easy for MSPs to manage
- Cons: Less flexibility for larger enterprises, minimal on-prem support
Fusion SIEM is a cloud-based SIEM solution tailored for MSSPs, MSPs, and smaller security teams. It offers core functionalities such as log collection, basic correlation rules, customizable dashboards, and compliance reporting. Fusion’s architecture emphasizes multi-tenancy, configurable pricing, and workflow automation to make SIEM more accessible.
While Fusion provides an affordable entry point, it lacks the advanced threat detection and analytics found in leading SIEMs. Its capabilities for custom modeling, fine-tuned algorithms, and third-party integrations are limited, and it’s not designed for massive enterprise scaling.
Fusion SIEM is best suited for basic security monitoring, particularly through MSSPs and MSPs. Its straightforward capabilities may be outgrown by organizations requiring more customization or sophistication.
Key Features
- Unified dashboards across customer accounts or environments
- Guided workflows for threat investigations and compliance reporting
- Automated response playbooks to block threats
- Purpose-built for MSSP/MSP delivery models
Why You Should Consider
Fusion SIEM offers an affordable and easy-to-manage cloud-based SIEM platform tailored for MSSPs and smaller security teams.
7. Sumo Logic
Sumo Logic provides a cloud-native SIEM-as-a-service for modern applications and infrastructure.
Key Features: Scalable data collection, machine learning-powered analytics, minimal maintenance
- Price: Starts at $83 per month billed annually
- Reviews & Ratings: 4.4/5 stars on Gartner Peer Insights based on 125 reviews
- Pros: Optimized for cloud, quick time-to-value, insightful analytics
- Cons: Limited on-prem support, less customizable than rivals
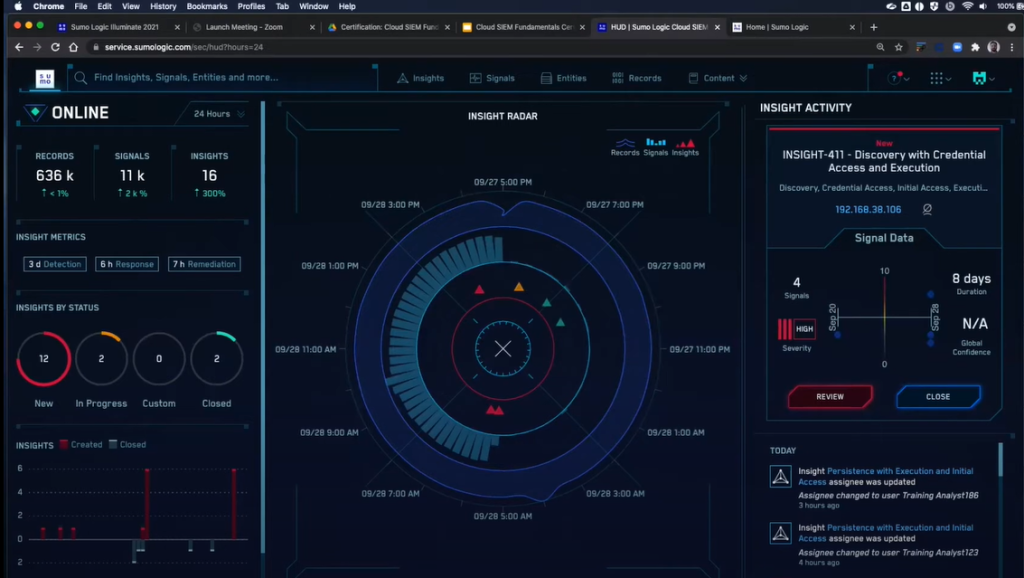
Sumo Logic focuses on cloud-native SIEM, offering analytics and compliance for modern, containerized applications across multi-cloud environments. It quickly ingests various telemetry streams for centralized monitoring and uses machine learning for threat detection.
The platform’s limitations include restricted support for traditional on-premises technology and less customizable workflows. Some users also report challenges in deriving value from its unique analytics architecture.
Sumo Logic is an appealing option for organizations adopting cloud-first strategies, particularly those migrating to AWS, Azure, or GCP. Traditional enterprises may find other SIEM tools more suitable, but Sumo’s focus on modern tech stacks is innovative.
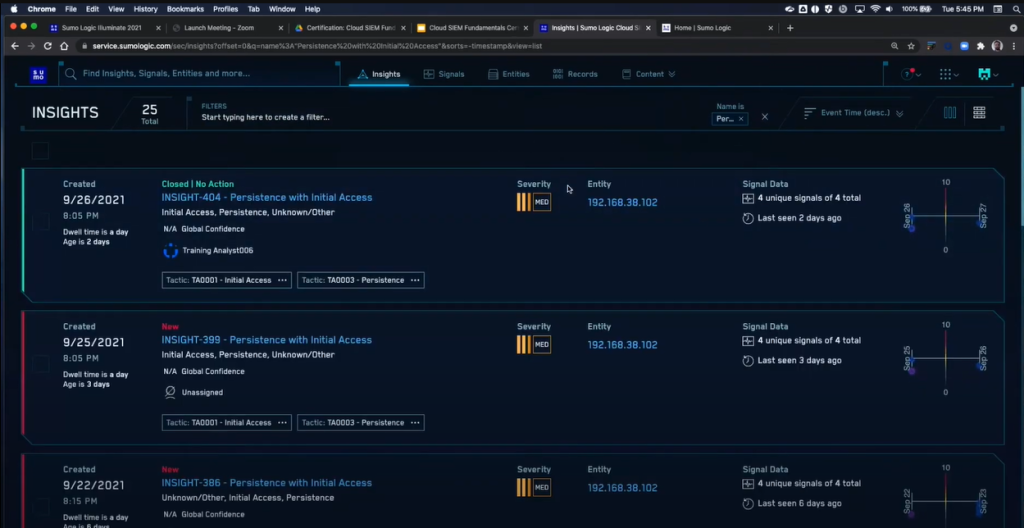
Key Features
- Unified visibility across cloud services, SaaS apps, and on-prem sources
- Machine learning detection of internal and external threat patterns
- Compliance reporting for standards like PCI, HIPAA, and GDPR
- Intelligent correlations across metric, log, and tracing data
Why You Should Consider
Sumo Logic provides fast time-to-value SIEM focused on cloud-native visibility, analytics, and minimized maintenance overhead.
8. McAfee Enterprise Security Manager
McAfee ESM delivers comprehensive SIEM capabilities alongside McAfee’s broader security portfolio.
- Key Features: Tight McAfee product integration, case management, advanced correlation engine
- Price: Starts around $25,000 annually for entry level
- Reviews & Ratings: 4.2/5 stars on Gartner Peer Insights based on 24 reviews
- Pros: Strong threat detection, robust compliance features, built-in case management
- Cons: Expensive, close McAfee ecosystem tie-in required to maximize value
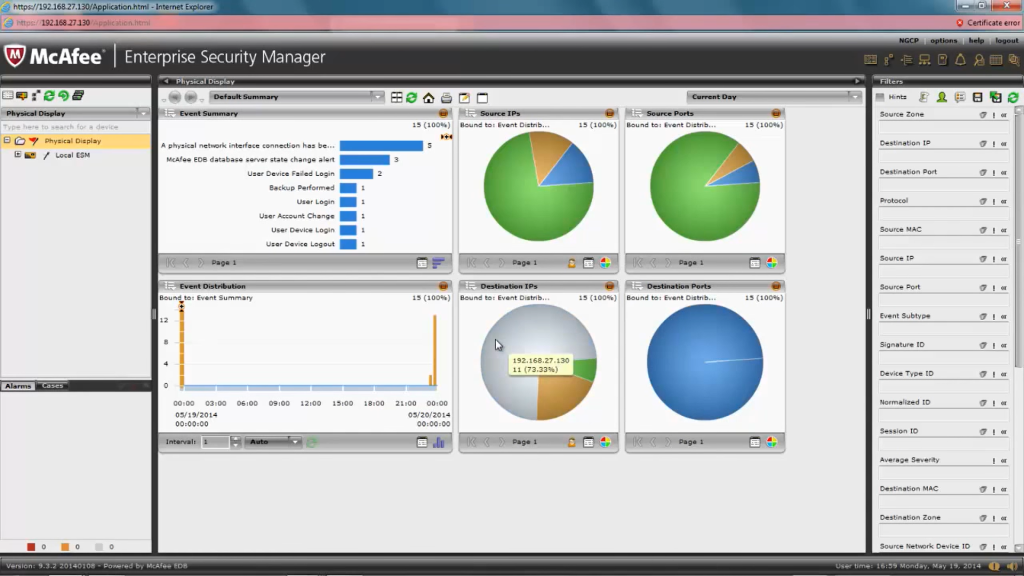
McAfee Enterprise Security Manager (ESM) enhances visibility, detection, and response by analyzing data from McAfee’s endpoint, network, and cloud environments. Its tight integration allows specific behavioral modeling, analytics, and threat intelligence, but this proprietary focus limits third-party integration.
As a standalone tool, ESM offers solid but not top-tier analytics, compliance reporting, and workflow customization. It functions best with standardized McAfee technology across infrastructure.
For organizations heavily invested in McAfee’s ecosystem, ESM provides a unified SIEM platform. However, as a general SIEM, it lacks the market-leading alternatives’ integration breadth, scalability, and configurability.
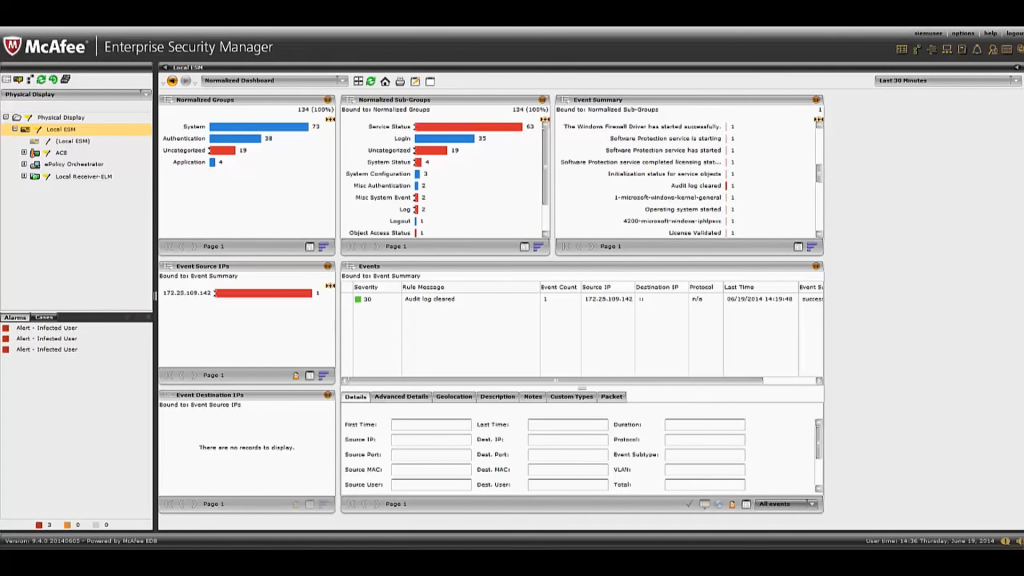
Key Features
- Case management workflow for handling incidents from detection to containment
- Integrated compliance reporting for PCI, HIPAA, ISO 27001, and more
- Tight observation and control of McAfee-protected endpoints and networks
- Advanced correlation engine across events, packets, flows, and alerts
Why You Should Consider
McAfee ESM is an ideal SIEM choice for organizations deeply committed to McAfee’s broad security ecosystem.
9. Salesforce Security Center
Salesforce Security Center provides unified visibility and compliance across Salesforce services.
- Key Features: Monitoring for Salesforce ecosystem, easy deployment, automated response and remediation
- Price: Starts at $12 per user monthly
- Reviews & Ratings: 4.7/5 on GetApp based on 3 reviews
- Pros: Native Salesforce environment integration, quick time-to-value, built-in automation
- Cons: Limited non-Salesforce support, lighter analytics compared to other SIEMs
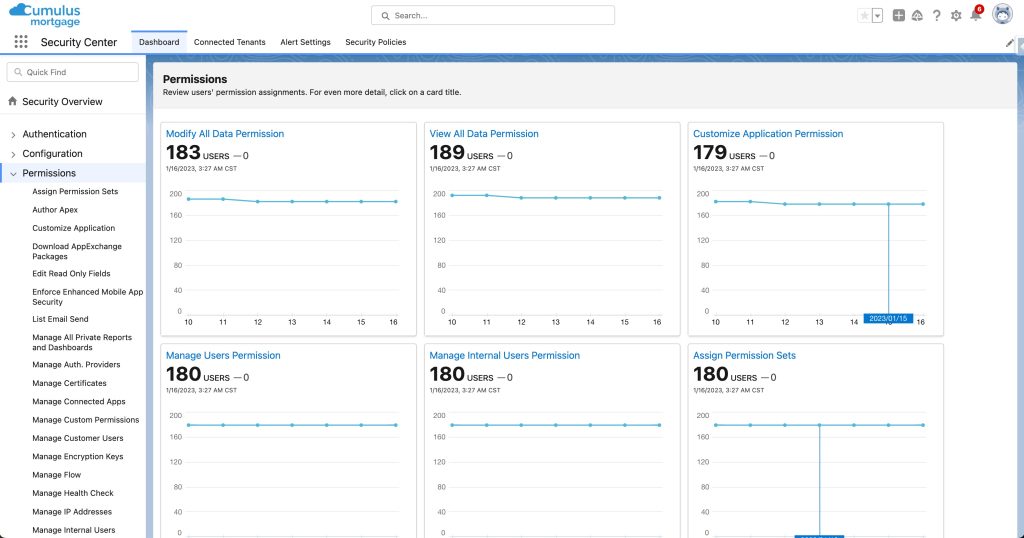
Salesforce Security Center offers integrated visibility and threat detection within the Salesforce ecosystem. Its tight integration with services like Einstein Analytics, Heroku, and Pardot enhances security and compliance for Salesforce users.
The platform’s limitations include restricted functionality for non-Salesforce environments and less advanced analytics capabilities compared to broader SIEM tools.
Salesforce Security Center serves as a specific solution for the Salesforce universe, but it falls behind traditional solutions for general enterprise SIEM capabilities. It adds value within the Salesforce-centric context but lacks expansive coverage.
Key Features
- Unified visibility and control across Salesforce services
- Automated responses like queue freezing upon threat detection
- AI-driven anomaly detection tuned for Salesforce environments
- Hundreds of pre-built reports, dashboards, and alerts
Why You Should Consider
Salesforce Security Center excels at providing integrated SIEM capabilities purpose-built for the Salesforce ecosystem.
10. Rapid7 InsightIDR
Rapid7 InsightIDR provides intelligent SIEM focused on usability and detection.
- Key Features: Behavioral analytics, easy cloud deployment, attacker linked response playbooks
- Price: Starts around $15,000 annually
- Reviews & Ratings: 4.7/5 stars on Gartner Peer Insights based on 38 reviews
- Pros: Intuitive workflows, powerful UBA, dynamic response actions
- Cons: Light compliance features, limited scalability for massive orgs
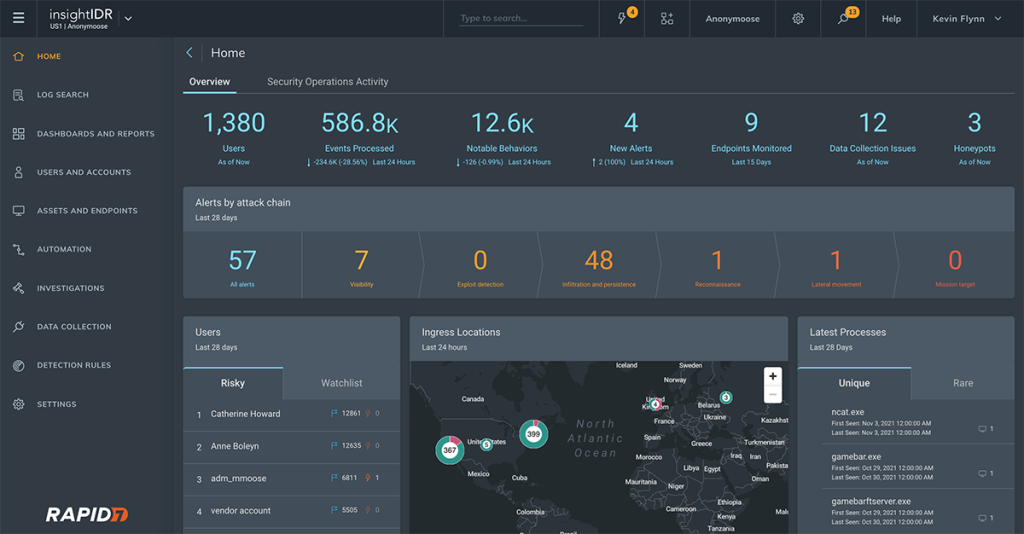
Rapid7 InsightIDR delivers SIEM capabilities with a focus on analytics, cloud scalability, and usability for mid-sized organizations. Its behavioral analytics excel in detecting compromised accounts, and integrated response workflows simplify threat containment.
Despite its strengths, InsightIDR lags behind top SIEMs in large-scale data ingestion and compliance report customization. Support for some legacy technology is also limited, and it hasn’t matched the deepest capabilities of tools like Splunk and IBM.
Rapid7 InsightIDR offers an accessible SIEM option for mid-market organizations, with a focus on automation, cloud delivery, and solid threat detection. While other solutions may better suit the largest enterprises, InsightIDR provides an approachable option for security analytics.
Key Features
- Behavioral analytics to detect compromised credentials and lateral movement
- Pre-built incident response playbooks with dynamic mitigation steps
- Unified cloud-based management across endpoints, network, logs, and users
- Intuitive search and automated reporting features
Why You Should Consider
Rapid7 InsightIDR combines strong UBA, workflows, and cloud delivery for expedited threat detection and response.
FAQs
What is the difference between SIEM and log management tools?
Log management tools concentrate on gathering and storing log data. SIEM solutions add correlating, analyzing, and contextualizing that data to detect threats. SIEMs incorporate log management capabilities plus advanced analytics and reporting for security teams.
Are SIEM tools suitable for small businesses?
Full-scale SIEM platforms are overkill for most small businesses. However, entry-level SIEM tools oriented towards SMBs are available with more basic capabilities, faster deployment, and lower licensing costs. When evaluating SMB-scale SIEM, prioritize essential features over advanced analytics.
How can I maximize the effectiveness of my SIEM tool?
Tuning use cases and correlations, establishing strong data sources, training personnel, and reducing false positives are key to getting the most value from SIEM software. Work with vendors during implementation and learn best practices for your specific SIEM platform. Supplement SIEM data with threat intelligence and vulnerability scanning insights for optimal threat detection.
Conclusion
SIEM platforms have become the nerve center for security operations, providing visibility, intelligence and workflows to augment resource-constrained teams. Organizations must identify core needs, then evaluate product fit, capability and budget when selecting solutions.
Mature products from vendors like Splunk, IBM and LogRhythm provide advanced analytics and suit large, complex enterprises. For SMBs, solutions like Securonix and Rapid7 balance intelligent detection on a smaller scale. Whether on-prem, cloud or SaaS-based, SIEMs have become indispensable tools for managing today’s vast and chaotic security landscapes.








